When only a Ghost (Ghoul) could freeze 5G connection and that too over-the-air

5G NR (New Radio) is one of the communication technologies that have and will continue to revolutionize the industry sector. With the increased communication speed, it is now possible to support high-end applications in diverse domains e.g., AR/VR, robotics and healthcare assistive services, among others. Thus, the reach of 5G NR goes beyond the standard smartphones and similar consumer devices.
As the usage of cellular protocols (e.g., 5G NR) becomes apparent in several critical domains (e.g., healthcare and industrial IoT), the security of such protocol implementations demands in-depth investigation.
While certain commercial products exist to test 5G user-equipment or UE (e.g., a smartphone) and/or 5G base station, they are highly expensive and unlikely to be accessible to average users and to small/medium scale industry sectors. Despite the cost, such equipment has limited capabilities to find previously unknown implementation vulnerabilities, especially in lower network layers (e.g., Data Link Layer). Back in 2021, the Wireless Security team led by Prof. Sudipta Chattopadhyay started thinking about low-cost, yet sophisticated technologies for in-depth and automated 5G security testing.
When the team started their research in 2021, it was a very risky and challenging research trajectory ahead. Firstly, there was no open platform for security testing of highly complex, multi-layered and closed 5G NR stack. Secondly, even the open-source software support for simply connecting to commercial-off-the-shelf (COTS) 5G devices was quite brittle, let alone for automated testing. Therefore, the risk of failure was extremely high. The team often recalls the sporadic stalemate they had reached in their research: there were often a period of several months when they were struggling to simply make connections with COTS 5G devices or trying to understand the 5G device logs, but without any success. Thankfully, the team had worked on Wireless security testing for Wi-Fi and Bluetooth before and such experience was immensely helpful to hang in there.
In the next two years from 2021 to 2023, the team has made a significant breakthrough to accelerate 5G security testing at scale.
The Inception of 5Ghoul Fuzzing
After at least two years of extensive research, (re)-engineering and technology development, the team had discovered their first (unknown) 5G modem vulnerability in April 2023 using their developed technology. Since then, their developed technology has already discovered 12 previously unknown vulnerabilities (12 CVEs) in 5G baseband modems from popular vendors e.g., Qualcomm and MediaTek. Most importantly, seven out of these 12 vulnerabilities are rated with “High” severity (the rest five have “Medium” severity) by the respective vendors, showing the importance of finding and patching such security flaws. Since all these vulnerabilities exist inside the code of 5G baseband modems from major vendors like Qualcomm and MediaTek, there are a substantial number of products in market that are affected by such vulnerabilities. For smartphones alone, there are more than 600 different smartphone models from Samsung, Apple, Huawei, Asus etc. that are affected. A detailed list of these affected phone models is available in 5Ghoul website.
The team had coined the term 5Ghoul, which is a combination of two words “5G” and “Ghoul”. In Arabian mythology, Ghoul is a demon like creature that distract travelers and upon successfully distracting them, the demon prays on them. The attacks that exploit 5Ghoul vulnerabilities likewise distract 5G devices to connect to a malicious base station and then launch attacks that drop or even freeze the connection that may sometimes require manual rebooting or manually removing the SIM card from smartphones. The following figure demonstrates the 5Ghoul attack scenario:
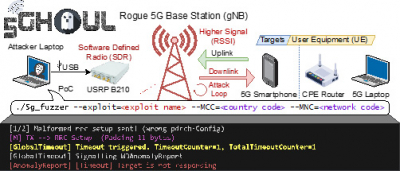
Figure 1: 5Ghoul Attack Scenario
During their research, the team had carefully thought about the design choices regarding the deployment of their technologies, especially in terms of the ease of usage for testing arbitrary 5G devices and the reliable over-the-air reproduction of attacks. The following figure shows the simplicity of deploying 5Ghoul testing:
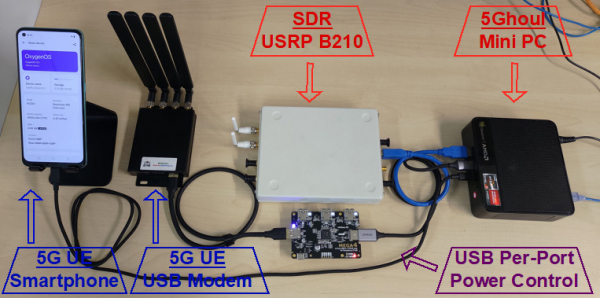
Figure 2: Deploying 5Ghoul Fuzz Testing Framework
If someone wish to test their 5G device, for example, a 5G USB modem or a 5G smartphone, the only thing user needs to do is to place their device as shown in Figure 2. The rest of the setup will work out-of-the-box. The security testing software runs locally on the Mini PC, while the USRP B210 is used to create the rogue base station. The entire setup is compact enough to fit in a backpack and could be carried easily in various places for live demonstration and testing.
USRP B210 in the 5Ghoul technology costs around ~2,400 SGD, thus making such technology easily accessible for research as well as small and medium scale enterprise. 5Ghoul employs systematic over-the-air Fuzzing. Thus, the impact of such technology is certainly not limited to the 5G (implementation-level) attacks already discovered by the team. Such systematic fuzzing is likely to discover many new attack vectors in a variety of 5G devices in near future.
Broader Impact
- 5Ghoul was publicly released on 8th December 2023 following a responsible disclosure period with Qualcomm and MediaTek: https://www.5ghoul.com. The discovery received significant media attention. Notably the key PhD student involved in the discovery, Dr. Matheus E. Garbelini (who is now a research fellow at SUTD) was interviewed by Channel News Asia. His interview segment is available here.
- The discovery was featured widely in technology media in Singapore and beyond. Notable coverage includes HackerNews, SecurityWeek, BleepingComputer, Hackaday, Heise (German), ZDnet (French), Edge Singapore, etc.
- The discovery has initiated alerts from regulatory agencies such as SingCERT and HSA, Singapore, considering that 5G modem vulnerabilities have many implications in industry sectors.
- The discovery of 5Ghoul has been awarded by Qualcomm and MediaTek with a bug bounty of 36,000 USD. Moreover, a Qualcomm spokesperson had publicly commended the research team in this SUTD media release.
- Since the public release of 5Ghoul code, there has been several independent reproduction of the attacks by Pen Testing industry like PentHertz (see here) that illudes on the reproduction of attacks even in Automotive devices. Additionally, researchers and practitioners have created more detailed videos on their own experience in reproducing 5Ghoul attacks.
- 5Ghoul security testing and attack scripts were released in public on 8th December 2023 (the same time as the release of 5Ghoul website). Since then, it has already attracted 400+ github stars, showing significant interest in the potential usage of such tools and reproduction of the attacks. 5Ghoul is available here.
About the Author
Sudipta Chattopadhyay is an Assistant Professor with the Information Systems Technology and Design Pillar, Singapore University of Technology and Design, Singapore. His general research interests lie in the broad area of cyber security including but not limited to security for AI, Wireless Technologies, and Internet of Things (IoTs). Together with his student, he discovered SweynTooth, BrakTooth and 5Ghoul, families of Bluetooth and 5G NR vulnerabilities that affect billions of devices worldwide. His research has been featured in WIRED, Channel News Asia, PC Magazine and Hacker News, among others. His discovery has also generated cyber security alerts from government regulatory agencies including CSA (Singapore), DHS, and FDA. He can be contacted via email: sudipta_chattopadhyay@sutd.edu.sg
